Passwords rule our digital lives. But there is a smart solution on the way: the passkey. But what exactly is that and how does it work?
Bert van Dyke
Hackers like that we often use the same passwords. Passwords that leak somewhere or are easy to guess can therefore easily be misused. They also like to let you log in to fake websites or log your keystrokes via malware. Remembering and entering those passwords again and again is often difficult for many users. Of passkeys can all these problems be solved. Apple will probably make this solution available in iOS 16, iPadOS 16, watchOS 9 and macOS Ventura around October. You no longer enter your username and password, but recognition of your face or fingerprint is sufficient.
 |
|
FIDO Alliance passkeys are supported by Apple, Google and Microsoft, among others |
Support
In 2021, Apple used the term passkeys for the first time at their annual developer conference. In March 2022, the FIDO Alliance (https://fidoalliance.org) adopted this new clear name for their discoverable Weauthn/Fido2password replacements that you have been able to save since 2018 in, for example, a YubiKey 5 USB stick. At the same time, she also announced that you could now use those passkeys on multiple devices via cloud services. In May and June, Google and Apple indicated that they would support this new technology this year; Microsoft will probably follow a little later. With so many big players on board, we will probably soon see this new, safe and fast way of logging in with many more apps and websites than we do now. Log in with Apple the case is.
Advantages passkey
The big advantage of a passkey is that you no longer have to change or enter passwords. There are no more passwords that can leak on websites. And because a passkey only works from your own smartphone on the original website, criminals can no longer steal your login details with a fake website.
Another nice extra is that extra checks via a code in an SMS or email are no longer necessary. Also the annoying one captchas (where you have to retype hard-to-read letters and numbers) become completely unnecessary. After all, if you log in via a passkey, it is already certain that the right person is logging in. Because everything also works very simply, this is also an ideal solution for the elderly who have trouble remembering all those passwords.
Because Apple is also adapting watchOS 9 for passkey, it will not surprise me if you will soon also be able to log in to all your Apple devices even more easily with your Apple Watch. After all, if you enter a PIN code when putting on your Apple Watch, you can now – as long as you continue to wear the Apple Watch – make large amounts of contactless payments without entering a PIN code.
Another application is to from Settings>Password share a passkey wirelessly with one or more other users via Airdrop. For example, you can easily have your partner log in with that passkey.
Apple offers space in the iCloud for endless passkeys. In addition, a recovery procedure with a 6-digit iCloud security code is available if you lose your iPhone and you no longer have any other Apple devices in use. With the YubiKey USB stick you can currently only store 25 passkeys and you do have a problem if you lose the stick. The YubiKey USB stick does support many more protocols, but due to its more complex use it is actually more suitable for more technical users and sensitive business applications where it is important that you cannot copy the passkeys.
By the end-to-end encryption Apple and Google cannot see or change your passkeys. Apple and Google have also both indicated that they are already working on a way to transfer passkeys for users who want to switch between an iPhone and Android device. Agilebits, the maker of the widely used 1Password app, also plans to support passkeys.
 |
|
Instead of a password, you store a passkey in your iCloud keychain |
Easy to use
As soon as a service supports passkeys, they can propose to create a passkey for you after you log in. You just have to choose Continue with TouchID (or FaceID) and after recognition of your fingerprint or your face, the passkey is stored in iCloud. Only the corresponding public key is sent to the website. So there is no longer a password that can leak out.
With a new website or app, you only need to enter a username and agree to save the passkey in a confirmation screen, as you see above.
In the future, if you choose Login with passkey, your smartphone recognizes that there is already a passkey for that website. As soon as you tap it, you can log in immediately after successful recognition of your fingerprint or face.
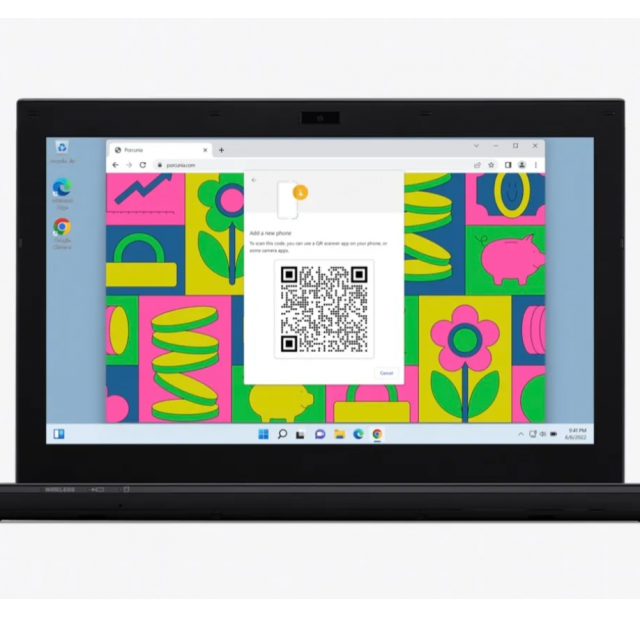
If you do not log in on your own computer, there will be no passkey on your computer and you will be presented with a choice screen to log in with a USB security key or a passkey on your iPhone, iPad or Android device. With the latter choice, a QR code will appear that you can scan.
 |
|
At https://apple-passkey.demo.hanko.io/ you can test to via a QR code |
If you do not log in on your own computer, there will be no passkey on your computer and you will be presented with a choice screen to log in with a USB security key or a passkey on your iPhone, iPad or Android device. With the latter choice, a QR code will appear that you can scan.
Very handy is that you will soon be able to log in easily and securely via iCloud on any computer with any app and website that supports passkeys. You will also be able to use passkeys on different computers via the password manager of Google’s Chrome browser.
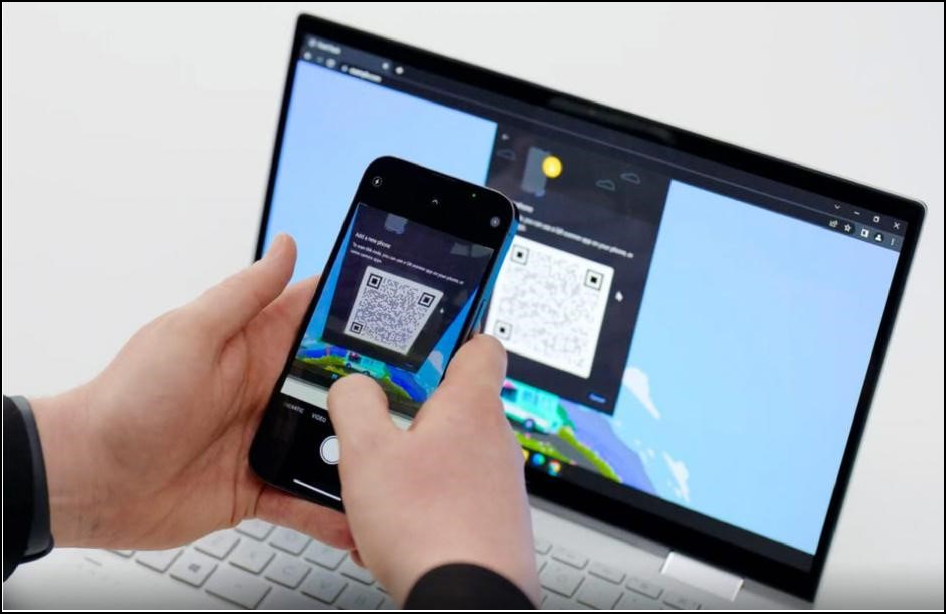 |
|
After a QR code scan and proximity check via Bluetooth, you can use passkeys on your iPhone |
Thanks to it Client To Authenticator Protocol (CTAP) you can also use your iPhone as authenticator use to securely log into an app or website on your computer. To do this, you scan the QR login code on your computer with your iPhone. This login is then safe via a secure communication between the two devices who trust each other. You do not run any risk phishing via a QR code from an email or fake website, because the login always fails if the QR code is not created very close to your iPhone. With the CTAP protocol used, it is checked via bluetooth whether both devices are really close to each other.
The technique
With a new website or app, you first enter a username, after which your device receives a message. Of FaceID or TouchID you prove that you are the owner of the device and two keys are created for every login. The secret private key is stored in your iCloud keychain. This makes that unreadable passkey also available on your other Apple devices that use the same Apple ID.
If you then choose to log in with passkey, a website or app sends a message asking to verify the user of the app with the standard authentication present on the device. If there is a passkey for that website in iCloud, you can confirm it and with a successful fingerprint or face verification you prove that you own the device and it calculates a digital signature with the private key of your passkey. That signature can check the server against your public key stored there during your registration. In case of a positive outcome, the service is 100% sure that it is you and you get access to the protected backend.
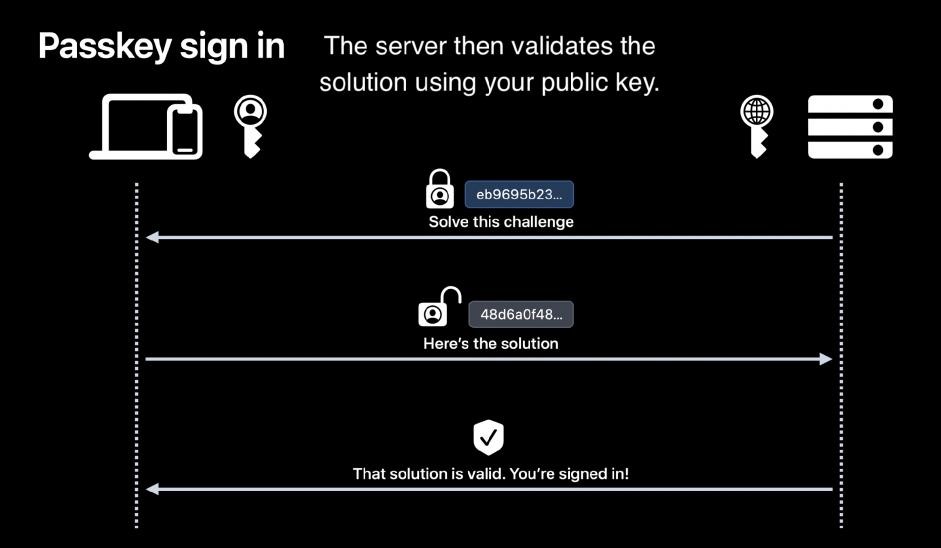 |
|
The website checks with the public key whether the digital signature has been set with the corresponding private key |