As soon as you browse the internet with your browser, you are quickly followed by numerous trackers. Extremely annoying for those who value their privacy, and all those accompanying advertisements are not exactly desirable. We show you how trackers work, but especially how you can (largely) prevent you from being followed closely.
When you surf to a website, the web server will see your IP address. Unless it is a fixed IP address that is linked to your domain name, for example, that IP address leads to an address pool with your internet provider and does not just betray your identity. You can check this by requesting your external IP address, for example via www.whatismyip.org, and then pass that on to a service like www.db.ripe.net/whois.
If you prefer to keep your IP address secret, you can use an anonymizing browser like Tor use, virtualized or not with Whonix. Or you can use a reliable VPN service to hide your IP address. But don’t think that this completely puts trackers on a dead end. They use even more means to follow you. You can read in this article which techniques these are and how you can protect yourself against them.
01 Browsers
One browser is not the other, even with your privacy in mind. If you think Tor is a bridge too far, Firefox is perhaps the most appropriate browser, if only because it is the only popular open source browser that does not use its own components. Admittedly, Chromium (on which Chrome is based) is also open source, but that is linked to Google. If you still like to stick to the Chromium concept, then it certainly falls Brave to consider. This free open source browser has some techniques built in that specifically target trackers and advertisements. And it has to be said: the latest Edge Chromium browser also pays extra attention to privacy and tracking prevention.
However, in this article we mainly focus on the most popular browsers: Chrome and Firefox.

02 Cookies
We will undoubtedly kick in an open door: cookies are still a common way to follow you. To prevent cookies from being stored permanently, you can surf in both Firefox and Chrome private mode. If you also want to limit tracking in normal browser mode, you should at least block third-party cookies. Suppose you visit site X that contains a link to the site of an advertising agency, and then you visit site Y where the advertising agency also has a link, then that agency can read the cookies previously placed and knows that it is the same person – at least, it is the same browser.
By default, third-party cookies are allowed, both in Chrome and in Firefox. In Chrome, you can block it as follows: tap chrome: // settings / content / cookies in the address bar and turn on the switch Block indirect cookies on from. You can also access this function via the menu, then go via the three dots to Settings / Advanced / Privacy and Security / Site Settings / Cookies and Site Data. In Firefox you enter about: preferences # privacy or navigate via the hamburger menu to Options / Privacy & Security where you at Browser privacy the option Adjusted ticked. We recommend that you check all options here. Specifically at Cookies you can then All third-party cookies Selecting. If that causes too many problems when surfing, then choose Cross-site and social media trackers.

03 Fpi
Firefox has a useful built-in feature against cross-site tracking via third-party cookies: First Party Isolation (fpi). The bottom line is that such cookies, like other surf data such as the browser cache, can only be accessed within the current domain and thus cross-site tracking is no longer possible. You activate this function as follows: Tap about: config in, search for first party and then double-click privacy.firstparty.isolate so that the value on true is being set. If this unexpectedly causes problems, you can soften that setting a bit by the two other options here false configure. If you want to enable or disable this fpi function with one click, you can use the extension First Party Isolation to install.
Although you will find the concept of site isolation in Chrome, it is more aimed at combating rogue attacks and does not prevent cross-site tracing. If you want to sharpen this function, tap chrome: // flags in, search for isolation, move Disable site isolation on Default and imagine Strict-Origin-Isolation in on Enabled.

04 Adblocker
To prevent web servers from collecting your surf data, you can activate the dnt (Do Not Track) function. In Firefox you can reach this function on the page about: preferences # privacy (or via the hamburger menu / Options / Privacy & Security) where you Always switches on at Send websites a “Do Not Track” signal to let them know you don’t want to be tracked. In Chrome you will find the function by chrome: // settings / privacy typing in the address bar or going through the menu to Settings / Advanced / Privacy and Security. Set the slide to this Send a no-track request with your browsing traffic. However, you should not expect much salvation from this: it is a simple request and most web servers do not respond to this.
So coarser guns are needed, in the form of an ad and content blocker. One of the better ones is uBlock Origin, available as a plugin for Chrome and Firefox. uBlock Origin works on the basis of filter lists and many domains are already blocked by default. You manage the plug-in from the dashboard: click on the corresponding icon to the right of the address bar and then on the button with the sliders. Open the tab Filter lists and preferably leave the check marks on all filter lists.
Sometimes it happens that websites refuse to show content as soon as they notice that you have an adblocker running. Then you basically have two options: you can add that website to the whitelist of uBlock Origin (all you have to do is click the icon and press the blue start button) or you can install an anti-adblock blocker over it (see box Anti-adblock blocker).

Anti-adblock blocker
Do you often feel that no content is displayed on websites because you have an adbocker installed? Then you can counter that by installing an anti-adblock blocker like Nano Defender in Chrome or in Firefox.
To integrate Nano Defender into uBlock Origin, you still have to perform a number of steps, such as here described. Carefully execute all instructions from the browser where you have installed both uBlock Origin and Nano Defender.
So at Step 3 you serve the tab Settings in the dashboard of uBlock Origin and check the box next to I am an experienced user. Then click on the gear icon behind this item and replace unset in the bottom line at userResourcesLocation by what it says. Confirm the adjustments by pressing the button Apply changes pressing. The other steps speak for themselves.
Then when you open the tab Filter lists you will open Adjusted see three Nano filters appear.

05 CDs
Many websites use javascript and gratefully use frameworks that include commonly used javascript functions. They usually get these frameworks from so-called content delivery networks, or CDNs, with Google being one of the most popular. That retrieval of frameworks from CDNs ensures that your IP address and other browser data also go to the CDN, so that you are also traced that way. The Decentraleyes browser plug-in, available for Chrome and Firefox, among others, ensures that the most commonly used frameworks become available locally to your browser, after which attempts to access a CDN are automatically redirected to the local framework. That protects your privacy and it also works just a little faster. You can check the situation before and after installing Test decentralized solutions. If you also have uBlock Origin running, it can ensure that the retrieval and updating of the local JavaScript libraries is prevented. On www.imgur.com/3YwdpGP indicated which domains you should add to the uBlock Origin exception list for it to work.

06 Scripting
You can of course go even further and block all (java) scripts instance. After all, it is often thanks to such scripts that web servers are able to identify you on the basis of all kinds of browser characteristics (so-called browser fingerprinting). With a simple mouse click you can click AmIUnique or Panopticlick find out to what extent your own browser is unique and therefore identifiable.
The popular browser plugin NoScript (available for Chrome and Firefox), however, let you decide which scripts and other content you want to run. Clicking on the NoScript icon will give you additional feedback. This way you can see which domains are involved and you can indicate whether you consider the external parts of the domain in question as Familiar (with which you allow them), Time. Familiar (permits only for the current visit), Not trusted (with which you block them) or Standard. In the Options you can indicate which elements you want to block or not for each zone. Open the tab General and click on each of the three zones: by ticking, you decide what you want to allow in each zone. On the tab Permissions you can adjust the trust zone for each website visited.

07 Referers
Just a small experiment: start Firefox, surf to www.google.nl, enter “computer! total” and click on the link that leads to the Techzle website. Then right-click on an empty spot on that web page and choose View Page Info. At Referring URL you now read https://www.google.nl. This is the so-called referer that is routed via standard http headers to a visited website. This practice is questionable for your privacy, because not only the website now knows where you come from, but also any advertising or social media networks that have content on that web page. Incidentally, such a URL can contain extra sensitive information – how about this referer: https://www.healthcare.gov/seeplans/85601/results/?county=04019&age=40&smoker=1&pregnant=1&zip=85601&state=AZ&income=35000?
However, in Firefox you can prevent this referer information from being passed on. Tap about: config on the address bar and search for network.http.sendRefererHeader. Double click on this item and change the default value 2 in 0 if you want to block all referers from now on. Set this up to 1, referers are only stopped when images are loaded on a page.
There is no anti-referral feature built into Chrome. However, the Referer Control browser plugin is available for both Chrome and Firefox. This even allows you to determine down to the site level how you want the browser to deal with these referring URLs.

08 Parameters
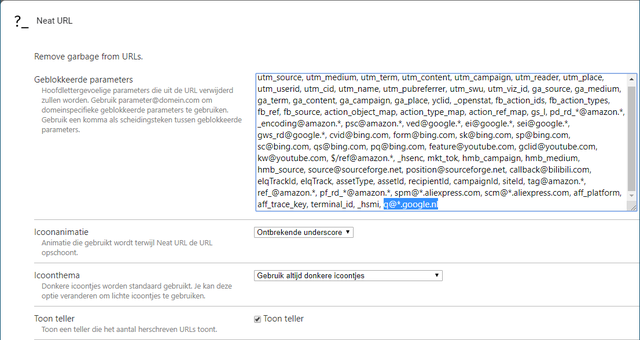
The URLs themselves may also contain information that may be useful to trackers, such as the “ValueTrack” parameters with Google Ads. For example, if an advertiser includes {lpurl}? Network = {network} & device = {device} in its tracking template, the url will become something like www.hetbedrijf.com/?network=g&device=t, so that the advertiser knows that you have clicked on that link via Google and from a tablet. Google Analytics also makes considerable use of url parameters (recognizable by & utm in the string).
The browser plugins ClearURLs and Neat URL, available for both Chrome and Firefox, strip such parameters from the url before passing it to the web server. We take a quick look at Neat URL here. The plug-in is automatically active after installation. To adjust something here, click on the corresponding icon with the right mouse button and choose Preferences. On the tab Options see you at Blocked parameters an overview of the parameters and you can add your own parameters, although according to certain rules. You must confirm your changes with Save preferences. For example, if you add paramname to this, it will parameter be banned from any url. An item like q@*.google.nl causes the parameter q exclusively in google.nl, although including subdomains (*), is cleaned up. However, this is not an example to implement yourself as this will cause your searches to go into www.google.nl stop working.