
© Starlink – Circular Terminal
A security researcher has managed to obtain a “root shell” on a Starlink terminal. But this attack required many hours of work and the creation of a dedicated circuit board, to be connected to the components of the equipment.
When a new technology service is available, the first thing hackers do is obviously try to hack it. And that’s exactly what happened with Starlink, the low-orbit satellite internet connection service created by SpaceX. At the Black Hat 2022 conference, which takes place in Las Vegas until August 11, security researcher Lennert Wouters, from KU Leuven University, demonstrated how to obtain a “root shell” on a Starlink terminal . Details of this attack will soon be available on GitHub.
A small “glitch” and the door opens
Let’s be clear: this hack is technically very complex and therefore difficult to reproduce for someone who knows nothing about physical attacks. If you’re lucky enough to have a Starlink terminal, don’t bother trying to do the same. To obtain this “root shell”, you must first remove the metal shell of the satellite dish, in order to be able to access the electronic components of the terminal. Then you have to connect over a driver circuit designed by Lennert Wouters.
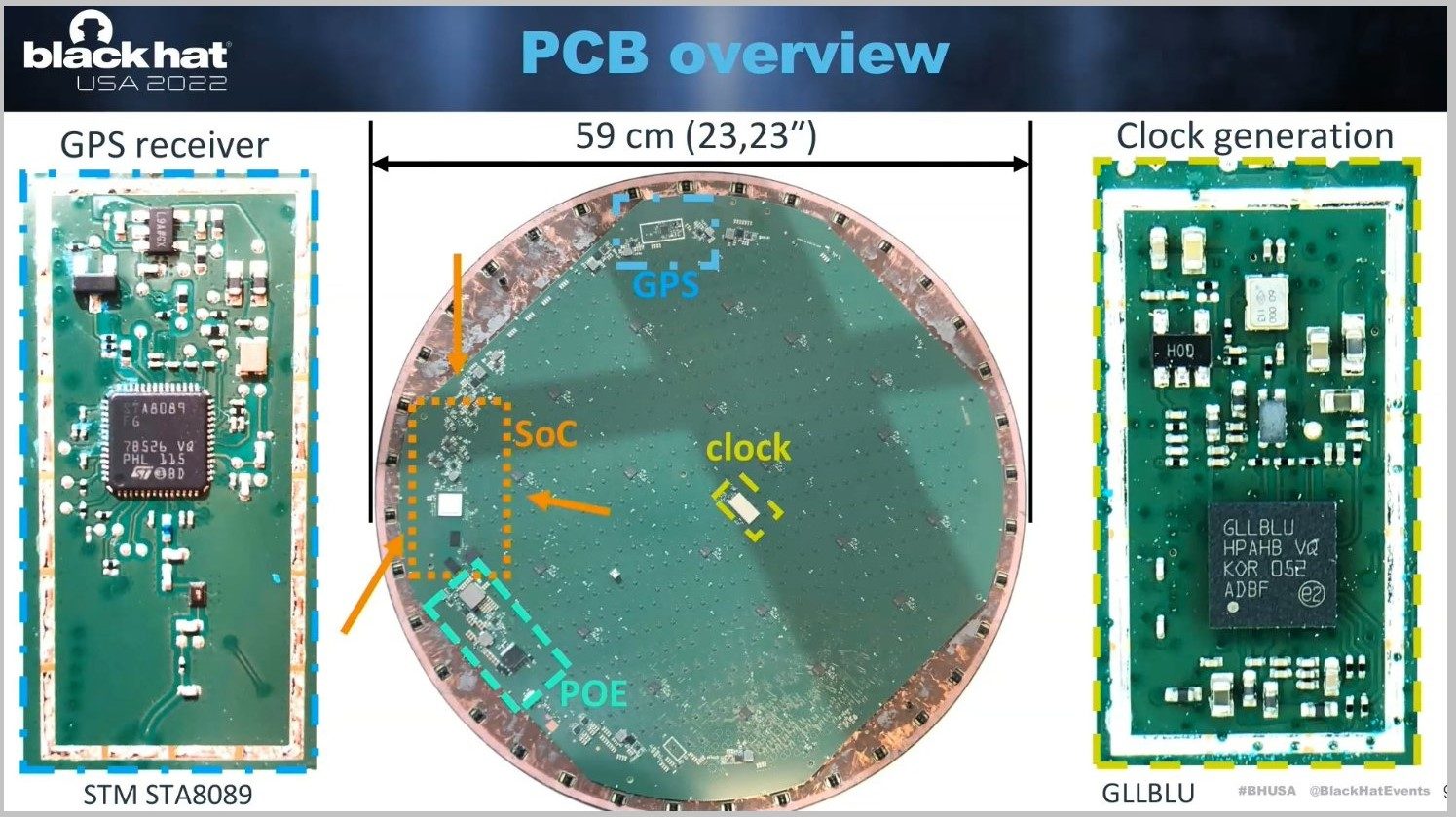
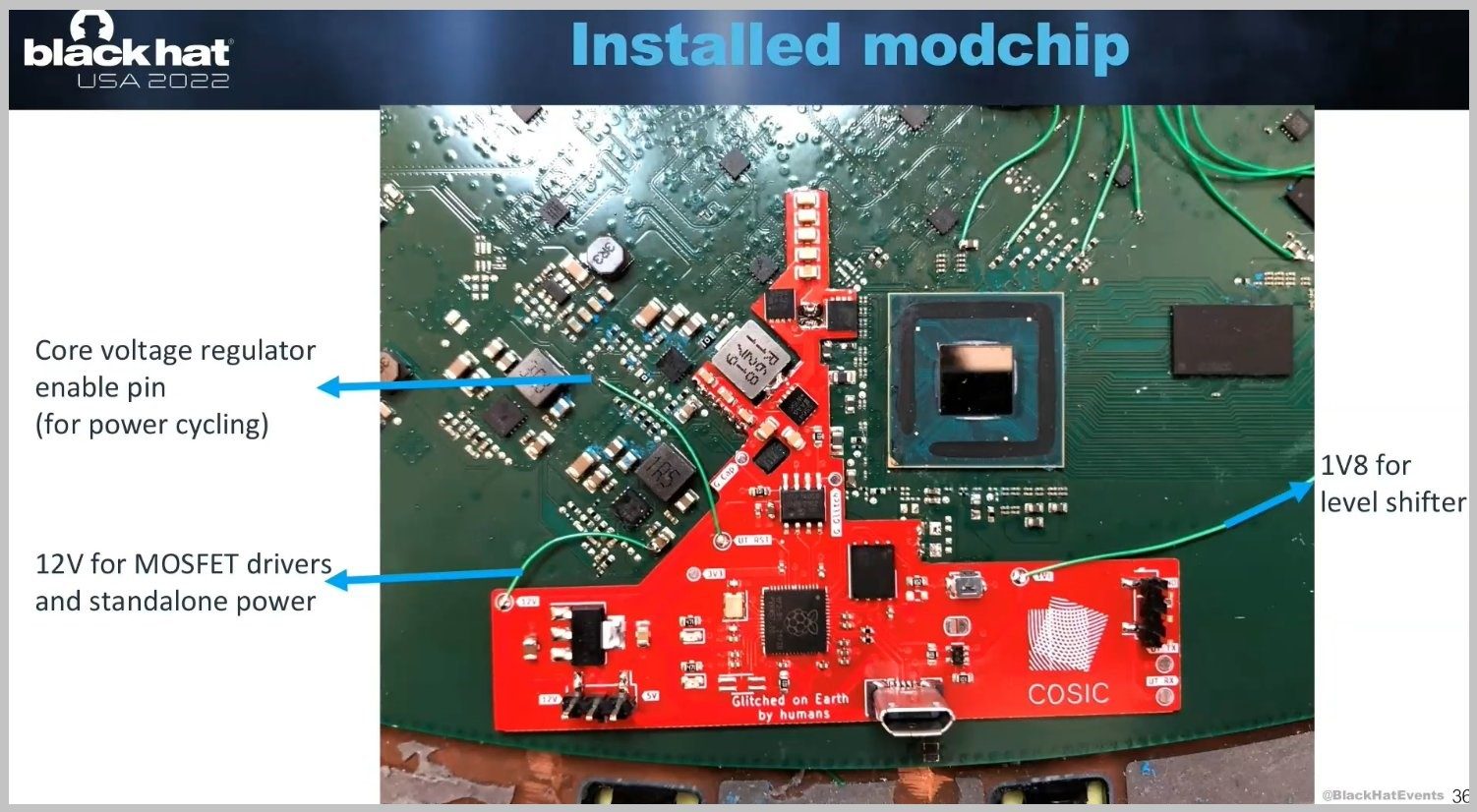
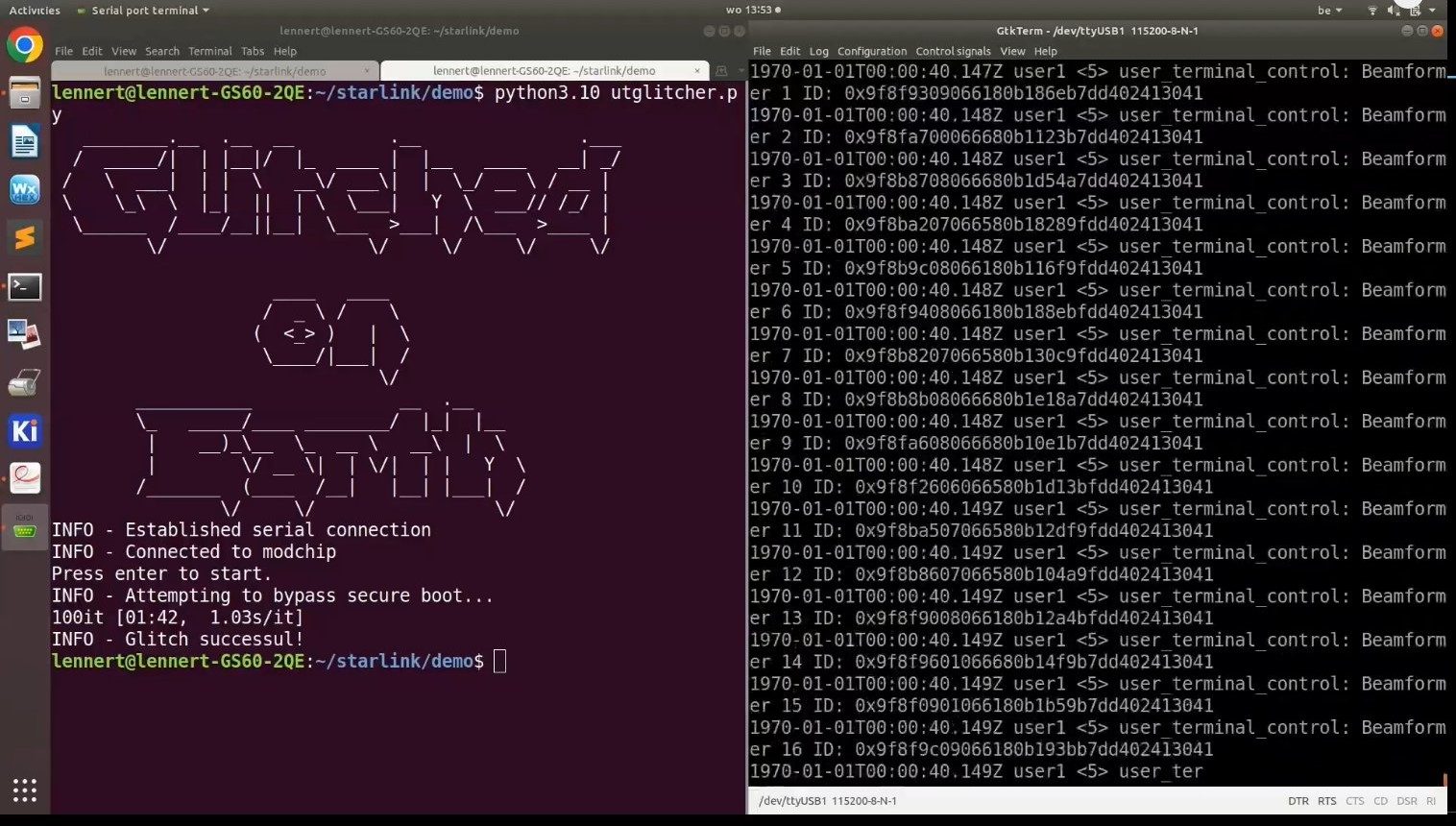
When the terminal is turned on, this circuit will inject small electrical disturbances (“glitching”) at the right time, which will have the effect of modifying the progress of the boot process (Secure Boot) and loading a modified version of the firmware. And finally, one gets full access to the system with administrator privileges. The researcher took advantage of his presentation to give a demonstration. It only took a few minutes to obtain this famous “root shell”.
On his attack circuit, Lennert Wouters took care to print the phrase “Glitched on Earth by humans”. It’s a nod to SpaceX engineers who printed the phrase “Made on Earth by humans” on the Starlink terminal circuit. A slogan that can also be found in the Tesla car that Elon Musk sent into space…
The analysis of the Starlink service is not yet complete. Thanks to this access to the system, Lennert Wouters will now try to explore the Starlink network and – why not – gain access to satellites or base stations. It is a goal that is far from devoid of interest. The start of the war in Ukraine showed that satellite communications are a priority target in the event of a conflict. And as the Starlink terminals are used on the ground of this war, it is probable that the Russian hackers are already working on the possible faults of the network.
It is a good quality equipment
But hackers risk breaking their teeth. Although he managed, after many hours of work, to find a way to access the terminal system, Lennert Wouters considers the security level of this product to be good. “There was nothing obvious to exploit. Getting root access was difficult, unlike other gear [de ce type]. And this access does not allow, in the immediate future, to carry out an attack on a larger scale, ”explained the security researcher in Las Vegas.
For their part, the leaders of SpaceX say they are delighted. In a communicated, they congratulated Lennert Wouters for his outstanding and “technically impressive” work. This is the first time they have faced an attack of this kind and they encourage all researchers to do the same, as part of a “bug bounty program”. They also take the opportunity to reassure users. All elements of the Starlink architecture would have been designed according to the principle of “least privilege” to limit the effects of a possible attack. Also, it would not be a priori possible to attack other terminals from a compromised terminal. We’ll see.
Black Hat 2022